What is Security Testing?
SECURITY TESTING is a type of Software Testing that uncovers vulnerabilities, threats, and risks in a software application and prevents malicious attacks from intruders to the system. Security Testing doesn’t guarantee the complete security of the system, but it is very essential to include security as a part of the testing process.
Purpose of Security Testing
The purpose is to identify all the possible loopholes and weaknesses of the system which might also result in a loss of information, revenue, repute at the hands of the employees or outsiders of the organization.
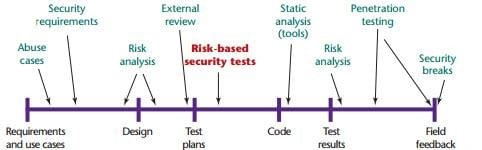
When Security Testing does comes in SDLC Phase
.
Types Of Security Testing
1. Vulnerability Scanning: – Vulnerability Scanning is performed by automated tools by scanning a system against to identify the risk to the organization and assist with remediation.
2. Security Scanning:-It involves identifying network, system weaknesses and later provides solutions for reducing that risks. Security Scanning will be performed by both the ways:-
-
- Manual Scanning
- Automation Scanning
3. Penetration Testing: – This kind of Penetration testing simulates an attack from a malicious hacker. The testing involves analysis of a particular system to check for potential vulnerabilities to an external hacking attempt.
Penetration testing was traditionally done manually by the trusted & certified security professional known as ETHICAL HACKER. The hacker works under and agreed scope to breach an organisation system in a controlled manner without causing any harm, damage to the system.
Now a days, automated penetration testing tools is providing similar benefits at less price with high testing frequency.
4. Risk Assessment: – This kind of testing involves analysis of security risks observed in the organization and recommended to control the measure to reduce the risk. Risk is classified as LOW, MEDIUM and HIGH.
5. Security Auditing:-This kind of testing do the internal inspection of applications and Operating System .An audit can also be done manually via line by line inspecting the code.
6. Posture Assessment: – This kind of testing combines security scanning, ethical hacking and risk assessments to show an overall security posture of an organization.
Security Testing Best Practices
Here, I am mentioning are few best practice that can help you implement Security testing and perform it successfully.
1. Server name and version should not display in Network.
2. Password should not display in the text format. (E.g. Removed type=“password” from the inspect element.)
[NOTE: Entered password should be display in the encrypted mode.]
3. Session Hijacking – Session ID should be change on Login/Logout and should not be in a fixed pattern.
4. OTP flooding should be restricted.
5. Bootstrap / jQuery / ASP .NET version should be latest for security purpose.
[NOTE: Tools & technology versions should not be vulnerable].
6. Http only flag should be set to “TRUE” in website‘s configuration file always.
7. Application should not allow to upload malicious (.exe) file in the application.
(E.g. rename any .exe file with .pdf and try to upload in upload document functionality.)
8. Session timeout should be properly configured in the application.
9. Application should not allow view the authenticated page from the cache option of the browser. Such as Error webpage.
10. Application should not allow to access authenticated pages through back button of the browser.
Steps to perform:
- Login into any application.
- Go to particular module or page.
- Logout from the application.
- Click on “Back” button of the browser and observe where browser was redirecting us.
(If browser is redirecting to that module or page which we was opened then it is an issue.)
11. Restriction should be there in password repetition. (Same password should not be repeat.)
12. Application should maintain audit trail properly. (Activity tracking should be there in application.)
13. Sensitive information should not display in open text format in application/ request/ response/ audit trail/ logs.
14. There should be limit on number of incorrect password retries while trying to login.
(This may lead to Brute force attack.)
15. Password complexity should be maintained.
(E.g. Password should be created via combination like Uppercase, Lowercase, Numeric, Special characters, etc.)
16. Input validation should be performed on the client-side as well as on the server-side.
- Accepts Only Known Valid Data – Character set should be defined for each field where input from the user is accepted. (E.g. ―A-Z, a-z, @,., 0-9, _ is a character set for a field that accepts user email.)
- Reject Known Bad Data. – Character set of bad data may be defined for the site that has to be rejected. (E.g. ―CREATE, DROP, OR etc.)
- Sanitize Known Bad Data – If there is a single quote (“‘”) in the data, it is replaced with double quotes.
17. SQL Injection.
- Escape Quotes.
- Sanitize the input or Remove Culprit Characters – Character sequences such as;, –, select, insert, *, and xp_.
- Limit the Length of User Input.
- Modify Error Messages – configure the error messages/ any message/ runtime error in such a way that it cannot be shown to outside users. (For E.g., Displaying server/ run time error like below image.)
18. Click Jacking should not be allowed – Application should not be open in any third party iframe.
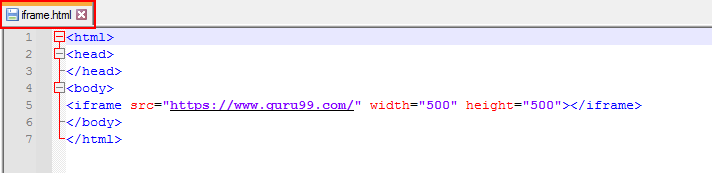
Step 1: In the given HTML code, enter the URL of website as a source of iframe tag. Now save it as a HTML file as shown below. After that, run the html file.
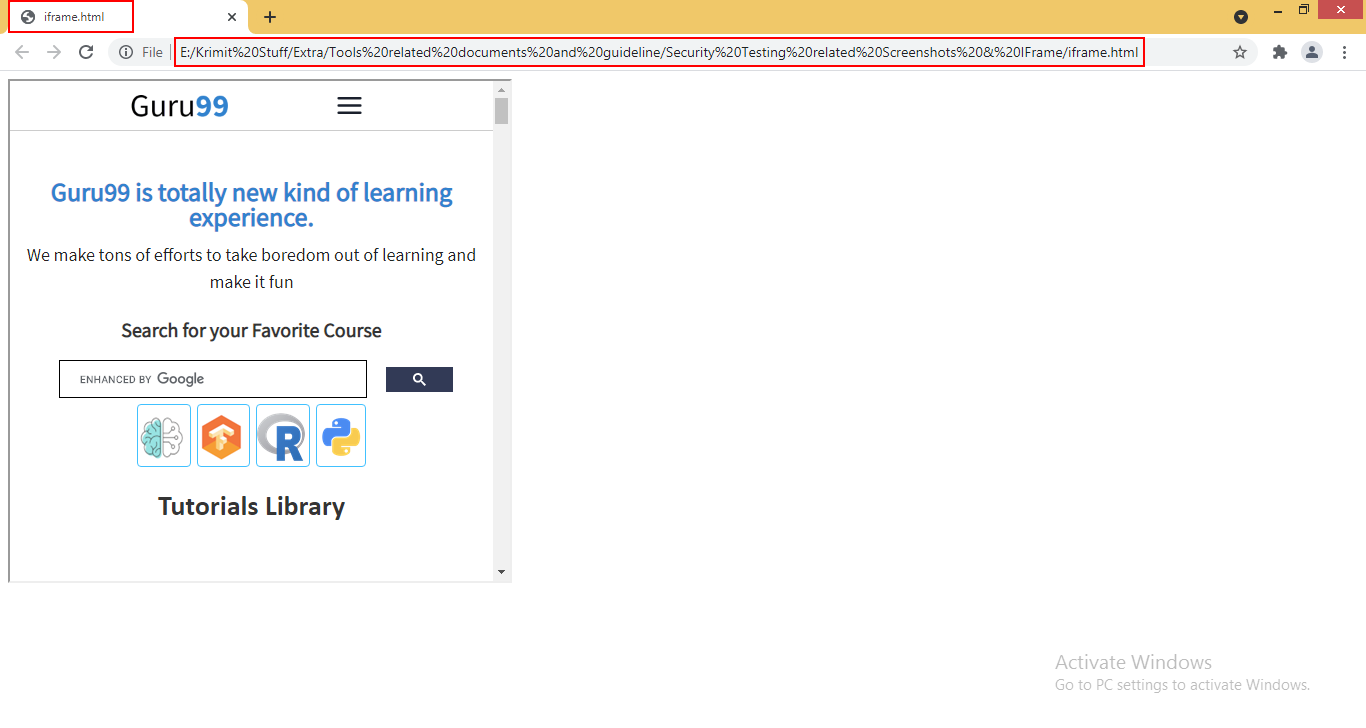
Step 2: As you can see, the website is able to open in frame which can also open in any third party website also.
19. Email flooding should be restricted in the application.
20. Auto fill should be disabled on login.
(For E.g., logged user names should not be displayed in the user name field suggestion.)
Conclusion
Security testing is the most important testing for an application to checks whether confidential data stays confidential and we are able to check whether the host is properly validated or not.
Security testing should be done as early as possible in Dev Cycle to secure Business Environment.
Author:- Garima Malik (Sr. QA Engineer)













Get in Touch